
 accesses since April 8, 1996
accesses since April 8, 1996  copyright notice
copyright notice

 accesses since April 8, 1996
accesses since April 8, 1996 In any event, when cyberspace comes to life it does so through virtual windows on workstations supported with client-server technology. The genesis of this virtual world was a technology that appears modest by modern standards: Telnet. Along with Email and ftp, Telnet was an early Internet killer application. What made Telnet distinctive was the fact that Telnet gave us inter-connectivity, the sine qua non of cyberspace. Telnet was not just a remote login procedure in a timesharing system. It was an inter-connectivity tool for every client and every server (in principle at least) on the Internet. The viability of this one general-purpose, pervasive program paved the way for all client- server technology to follow. It was an early milestone in the evolution of cyberspace.
What followed is miraculous even by modern computer industry standards. From 1983 when Arpanet went "public" to the present, the Internet has grown to 25 million users on 2 million computer systems using 10 thousand subnets [6]. Monthly growth rates are estimated to be in the double digits. The usage statistics depicted in Figure 1 are typical for modern network information centers.
First, consider the case of Internet "white pages." These resources (Whois, X.500, Knowbot Information Systems (KIS), Netfind, etc.) are directory services for the Internet itself. However, even within that small group there are large differences. Whois is a centralized directory based upon the Unix Finger program. X.500 is a decentralized directory. KIS isn't really a directory service at all, but is a directory service locator. That is, KIS uses existing directories to find Internet users. Netfind is yet an entirely different animal. It doesn't limit its domain to network directory facilities like Whois and X.500. It will scour the net for Internet users on individual servers.
Second, let's consider the case of Emailers. There are scores of Email systems with widely varying capabilities and vastly different levels of sophistication. Some, like Elm, betray a 1970's human factors orientation. Others, like cc:mail and LaMail are modeled after today's word processors. Some mix the old with the new. Pine, for example, has an interface that is clumsy and stiff by modern standards. But it allows the Emailer to attach multimedia files to the message - forward thinking even for the 1990's. Like the net directory services, they span the spectrum of that which is possible and desirable.
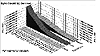 Figure 1. The usage statistics for modern network information centers.
Figure 1. The usage statistics for modern network information centers.
We offer the following categorization (see Figure 2) as one of
many perspectives on current Internet client-server resources.
FUNCTIONALITY: On our account, there are six basic categories of Internet resources. Transfer programs [t] facilitate the transfer of files. Directory programs [d] are the Internet's 'phone books. Locators [l] ferret out information on the net. Organizers [o] attempt to virtually organize network resources for a particular user in much the same way that a database schema does. Communications programs [c] deal with message transmission - for brevity, we focus only on interpersonal communication here. Next, we have the client- server browsers [b]. If Internet is the backbone of cyberspace, the browsers are its blood supply. Browsers open the Internet to the virtual consumption of information - text, graphics, sound, video. This information is right at your fingertips irrespective of it's physical location or source. Finally, we have the remote login software, Telnet [t], let's us take advantage of most of these resources even without the client-side software on our workstation.
DOMAINS: The resource domain describes the nature of the material with which it works. Directory systems [d] work with internal network information like names of users and domains. Document domains [d], files-oriented systems [f] and message passing domains [m] are self-explanatory. General purpose [gp] resources support all of the above, and multimedia as well.
TOPOLOGY: This is the layout of the network as perceived by the user and his computer. Although more fine-grained distinctions are possible, we choose to distinguish only between point-to-point [p] and Network [n] topologies. PTP may be thought of as a direct link to some Internet resource - two objects linked by fiber, as it were. Network topologies may be viewed as graphs. One may 'virtually' move through the net via strands of interconnected nodes. Cyberspace requires a network topology.
GUI:Whether the Internet resources supports graphical user interfaces.
HYPERLINK: Whether the data is linked non-linearly with both document-document and document-server links.
MULTIMEDIA: For a first pass, we distinguish between text and multi-media support. On our view, multi-media includes sound and video.
Given our concern for simplicity, our classification scheme let's things fall through the cracks. Internet Talk Radio is a new form of digital mass communication - the Internet radio station as it were. The audio tracks of the program are digitized and stored at an Internet ftp site for downloading and playback at your workstation. This facility really falls within the rubric of mass communication via cyberspace which is not covered in this article.
The same holds true for the new wave of audio/visual offerings. These programs fall into four basic groups: teleconferencing software, whiteboard software that supports interactive document creation, audio/video annotation software that adds sight and sound to basic text/graphics transmissions, and algorithmic animation and visualization that is kind of an upscale Telnet. While presently LAN creatures, these programs will soon be client-server offerings on the net. Their importance derives from the fact that they add human interaction to the virtual terminal.
Finally, there is MUD? Multi-User Dungeons were originally network game programs. Now they have interactive educational programs bearing the MUD look-and-feel. The MUD region of cyberspace is a nebulous one.
While Figure 2 reveals some variations between client-server programs, it is not complete. As any cutting-edge Web surfer will confirm, within each category there are products with significant differences. Webbers will confirm that such clients differ significantly between each other in terms of functionality. Clients in one family will have a very different look-and-feel from those in another, even when written for the same environment. There is as much variety within the family of Mosaics as there is between families.
The point is that even when one looks only at one environment, there is little orthodoxy when it comes to software design and engineering. The closest thing to a standard that we have is Mosaic. Even there the variation within products is noteworthy.
To illustrate, consider the functionality of a sample of current Web navigator/browsers (Figure 3). While the general structure of the display page is predictable due to the html compliance required by Web, major differences remain. In the Netscape Mosaic, for example, the search engine is integrated with the navigator/browser - a non-trivial undertaking and well ahead of its peers in this area. Win Tapestry supports a hierarchical hotlist folder organization, unmatched by the other products. Since hotlists and bookmarks don't scale well, this is an also an important feature for the serious user as is the ability to edit, import and export hotlists and bookmark files to foreign products. Web Explorer on the other hand has a well-developed cyberlog or itinerary history, and like Air Mosaic has a full-screen or kiosk option that is important in presentations to minimize the distractions produced by the workstations' background desktop. In short, all have advantages and shortcomings when it comes to features which serious users would consider to be important. These are obvious from even an incomplete overview such as that in Figure 3.
compliance - Current strengths include proxy client support for the most popular protocols, which is a sine qua non for penetrating firewalls; interface protocol compliance for the most popular Internet environments (Gopher, WAIS, WWW, ftp, etc.); and telecommunication protocols (SLIP,PPP,TCP/IP). Most important weakness is in terms of multimedia support. It is not unusual for WWW clients to hang up in different areas of cyberspace even though they claim compatibility with the same standards.
integration - The successful products of the future will offer seamless integration to a wide-variety of utilities, most of which are as yet undefined. Now the two most important utilities for cyber- surfing are search engines and external perusers (video and audio), and in these areas current products receive low marks. Few clients support robust native viewers and even fewer include search engines. Successful products in this area will be those which are compliance with the broadest range of third-party perusers since there is no way to tell which of the incompatible audio and video file formats will endure. Peruser development will be as random and unpredictable as were graphics applications were a decade ago. The same may be said of search engines as cyberspace spawns increasing numbers of spiders, worms and wanderers. Those vendors who focus on the integration of native utilities rather than compatibility with third-party products will lose any competitive edge surely and quickly.
extensive commercialization of the market - We are already seeing that. NCSA, the original developer of Mosaic, has already licensed the software for commercial development. At least three aggressive companies are currently marketing NCSA licensed Mosaic progeny (Netscape, Spyglass and Air). This trend will continue until nearly all of the innovation comes from the commercial side.
migration to Windows environment - This controversial claim follows from the observation above. The numbers tell the story: marketing to 75 million Windows users has greater potential return that marketing to 5 million Macintosh users or 2 million Unix users. While these approximations may be slightly off, the message comes through plain and simple: the big bucks are in the Windows market, and that is where most vendors will place their capital. Over time more players will enter the game, which will increase competition and cause the developers to become more focussed on the major markets. On our view the long-term market for Macintosh client-server browsers looks grim. We predict that Unix will continue to be the host of choice for much of the technological innovation, but that these innovations will be quickly ported over to Windows or its successor for refinement and commercialization.
information customization - Finally, we come to that aspect of cybersurfing which relates to our own research. We believe that the next 3-5 years will see a change from an information-provider orientation to information services to that of the information-consumer. Information customization is an important first step in that regard. Information customization may take many forms from transformations of information to the non-prescriptive non-linear traversal of documents, but in all cases it subscribes to the principle of information utilitarianism whereby the value of information is determined by its usability to some information consumer at some moment in time. For further information consult [1],[2],[3].
For the next few years, the greater interest will be with the hardware and software innovations. This is true with any technology in its infancy. As cyberspace technology matures, the interest will gradually turn away from the technology and toward the content of the information conveyed. As a society, we are in the fascination phase of this technology - much as our grandparents were with their cumbersome and unsophisticated crystal radio sets. Quickly, we shall come to expect perfection from our cyberspace products and will balk at the prospect of perusing cybermedia that has not been customized. By the end of the decade, as the bandwidth and efficiency of the nets increase, cyberspace will support a full range of interactive, participatory, three- dimensional, omni-sensory, virtual experiences. By mid-century it may be exceedingly difficult to distinguish between the virtual experience in cyberspace and its veridical counterpart.
Since Cyberspace is in its infancy and we don't yet depend upon it for our survival, it can be still be enjoyed. Like a good cruise, much of the fun is just going somewhere. Toward that end, you might enjoy leaving from my dock: url= http://berghel.net.
References:
[1] Berleant, D. and H. Berghel, "Customizing Information: Part1-Getting we need when we want it", IEEE Computer, 27:9, pp. 96-98 (1994).
[2] Berleant, D. and H. Berghel, "Customizing Information: Part 2 - How successful are we so far?", IEEE Computer, 27:10, pp. 76-78 (1994).
[3] Berghel, H. and D. Berleant, "The Challenge of Customizing Cybermedia", Heuristics: The Journal of Knowledge Engineering, 7:2, pp. 33-43, (1995).
[4] Berghel, Hal, "Cyberspace Navigation". PC AI Magazine, 8:5, September/October, pp. 38-41 (1994)
[5] Gibson, William, Neuromancer. Ace Books, New York (1984).
[6] Gilster, Paul, The Internet Navigator. Wiley, New York (1993).